Is it possible that your WordPress site has been hacked?
Hackers frequently install a backdoor to ensure that they can access your website even after you’ve secured it. There’s no stopping them until you can get rid of that backdoor.
We’ll teach you how to discover and fix a backdoor in a hacked WordPress site in this post.
How to Tell if Your Website Has Been Hacked
If you’re running a WordPress site, you need to be concerned about security. This is due to the fact that websites are attacked 44 times every day on average.
Our definitive WordPress security tutorial will teach you how to keep your site safe.
What if, though, your website has already been hacked?
A decrease in website traffic or speed, the addition of malicious links or unfamiliar files, a defaced home page, an inability to log in, suspicious new user accounts, and more are all symptoms that your WordPress site has been hacked.
Cleaning up a compromised website may be very unpleasant. In our beginner’s guide to repairing your hacked WordPress site, we walk you through the procedure step by step. You should also scan your documents.
What Is a Backdoor?
A backdoor is a piece of code that allows a hacker to get access to a website’s server while staying undetected and circumventing the standard login process. It allows a hacker to obtain access to your website even after you’ve discovered and fixed the vulnerable plugin or vulnerability.After the user has gained access, backdoors are the next stage in the hacking process. Our tutorial on how WordPress sites get hacked and how to avoid it might help you figure out how they did it.
Backdoors are notorious for surviving WordPress updates. That implies your site will stay vulnerable until all backdoors have been discovered and fixed.
What Are Backdoors and How Do They Work?
Some backdoors are merely admin usernames that have been concealed. They allowed the hacker to log in normally by entering a username and password.
password. You have no idea that someone else has access to your website since the username is masked.
Hackers using more advanced backdoors may be able to run PHP code. They use their web browser to manually submit the code to your website.
Others feature a full user interface that lets people send emails as your WordPress hosting server, do SQL database queries, and do a lot more.
Some cybercriminals will leave several backdoor files. They’ll upload another after that to confirm they have access.
Where Can You Find Backdoors?
Every time we’ve discovered a backdoor, it’s been camouflaged as a WordPress file. Backdoor code is typically kept in the following areas on a WordPress site:
password. You have no idea that someone else has access to your website since the username is masked.
Hackers using more advanced backdoors may be able to run PHP code. They use their web browser to manually submit the code to your website.
Others feature a full user interface that lets people send emails as your WordPress hosting server, do SQL database queries, and do a lot more.
Some cybercriminals will leave several backdoor files. They’ll upload another after that to confirm they have access.
Where Can You Find Backdoors?
Every time we’ve discovered a backdoor, it’s been camouflaged as a WordPress file. Backdoor code is typically kept in the following areas on a WordPress site:
Theme for WordPress,
The wp-includes folder contains PHP scripts that WordPress needs to function properly. Because most website owners don’t check to see what the folder contains, it’s another location where we locate backdoors.
We’ve discovered a number of backdoors.
Here are some examples of backdoors that have been posted by hackers. The backdoor was found in the wp-includes folder on one of the sites we cleaned up. The file was called wp-user.php, which appears to be harmless enough, but it doesn’t exist in a standard WordPress installation.
In another case, a PHP file titled hello.php was discovered in the uploads folder. The Hello Dolly plugin was used to hide it. Strangely, the hacker placed it in the uploads folder rather than the plugins folder.
We’ve also discovered non-standard backdoors.
How to Find a Backdoor in a Hacked WordPress Site and Fix It
You now understand what a backdoor is and where it may be found. Finding it is the tough part! Cleaning it up after that is as simple as removing the file or code.
1. Look for code that might be harmful.
A WordPress malware scanner plugin is the simplest approach to search your website for backdoors and vulnerabilities. Securi comes highly recommended since it helped us prevent 450,000 WordPress assaults in three months, including 29,690 backdoor attacks.
They provide a free WordPress Sucuri Security plugin that allows you to check your site for common attacks and strengthen your WordPress security. The commercial edition includes a server-side scanner that checks for backdoors and other security vulnerabilities once every day.
More information may be found in our guide.
Learn how to inspect your WordPress site for possible harmful code in our guide.
2. Remove the Plugins folder from your computer.
It takes time to go through your plugin directories for suspicious files and code. There’s no assurance you’ll locate a backdoor since hackers are so cunning.
The best course of action is to erase your plugins directory and then reinstall them from fresh. This is the only method to ensure that your plugins are free of backdoors.
You may use an FTP programme or your WordPress host’s file management to get to your plugins directory. If you’ve never used FTP before, check out our tutorial on how to upload files to WordPress via FTP.
You may use an FTP programme or your WordPress host’s file management to get to your plugins directory. If you’ve never used FTP before, check out our tutorial on how to upload files to WordPress via FTP.
To go to your website’s wp-content folder, you’ll need to utilise the programme. After that, right-click on the plugins folder and choose ‘Delete’.
’.
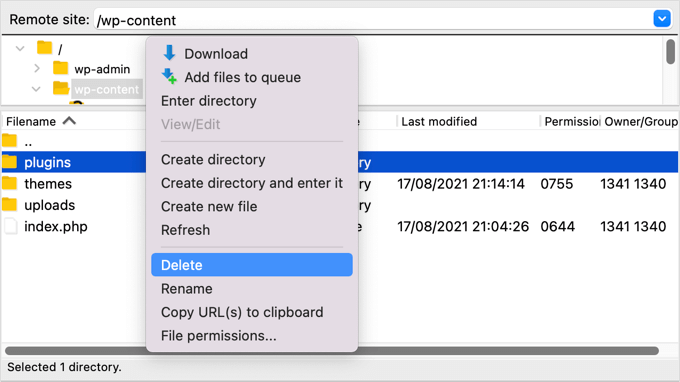
3. Delete Your Themes Folder
Similarly, rather than wasting time looking for a backdoor in your theme files, it’s easier to just remove them.
After you’ve deleted your plugins folder, go ahead and delete the themes folder as well.
You don’t know if that folder had a backdoor, but if it did, it’s no longer there. You’ve just saved time and eliminated an extra attack point.
You may now reinstall any themes you require.
4. Look for PHP files in the Uploads folder.
After that, go through the uploads folder and check sure there aren’t any PHP files there.
Because it’s meant to be in this folder, there’s no reason for a PHP file to be there.
.
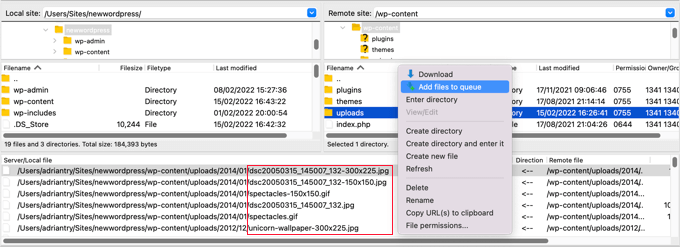
You can now scroll through the list looking for files with the .php extension.
Alternatively, advanced users who are familiar with SSH can write the following command:
|
1
|
find uploads -name "*.php" -print |
5. Delete the .htaccess File
Some hackers may add redirect codes to your .htaccess file that will send your visitors to a different website.
Using an FTP client or file manager, simply delete the file from your website’s root directory, and it will be recreated automatically.
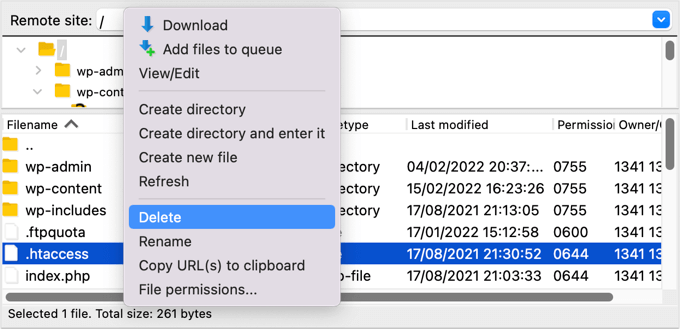
If for some reason it isn’t recreated, then you should go to Settings » Permalinks in your WordPress admin panel. Clicking the ‘Save Changes’ button will save a new .htaccess file.
6. Check the wp-config.php File
The wp-config.php file is a core WordPress file that contains information that allows WordPress to communicate with the database, the security keys for your WordPress installation, and developer options.
The file is found in your website’s root folder. You can view the file’s contents by selecting the Open or Edit options in your FTP client.
Now you should look at the contents of the file carefully to see if there is anything that looks out of place. It might be helpful to compare the file with the default wp-config-sample.php file which is located in the same folder.
You should delete any code that you’re certain doesn’t belong.
7. Restore a Website Backup
If you’ve been creating frequent backups of your website but still have concerns that it’s not totally clean, restoring a backup is a viable option.
You’ll need to wipe your entire website and then restore a backup that was taken before it was hacked. This isn’t for everyone, but it will give you complete peace of mind that your site is secure.
See our beginner’s guide on restoring WordPress from backup for more details.
How to Prevent Hacks in the Future?
Now that you’ve cleaned up your website, it’s necessary to beef up its security in order to avoid future hacks. When it comes to website security, it doesn’t pay to be cheap or inattentive.
1. Back up your website on a regular basis.
Today is the day to start making regular backups of your website if you haven’t already.
WordPress does not have a backup system built-in. However, there are numerous excellent WordPress backup plugins that allow you to backup and restore your WordPress site automatically.
One of the greatest WordPress backup plugins is UpdraftPlus. It enables you to create automated backup schedules and will assist you in restoring your WordPress site in the event of a disaster.
Learn more about backing up and restoring your data in our guide.

2. Install a Security Plugin
When you’re busy running your business, it’s impossible to keep track of everything that happens on your website. As a result, we recommend that you utilise a security plugin such as Sucuri.
Sucuri comes highly recommended since they excel at what they do. CNN, USA Today, PC World, TechCrunch, The Next Web, and other major magazines concur. Furthermore, we rely on it to keep WPBeginner safe.
3. Improve the security of WordPress login
It’s also critical that you improve the security of your WordPress login. When users establish accounts on your website, the best place to start is to require them to use secure passwords. We also suggest that you begin utilising a password manager such as 1Password.
The next step is to implement two-factor authentication. This will be beneficial.
This will safeguard your website from brute force assaults and stolen credentials. This implies that even if a hacker has your login and password, they will be unable to access your website.
Finally, you should keep the number of login attempts in WordPress to a minimum. Users can input passwords as many times as they wish on WordPress. If you lock a user out after five failed login attempts, a hacker will have a much harder time figuring out your login credentials.
4. Keep the WordPress Admin Area Safe
By preventing unauthorised access to the admin area, you may prevent numerous typical security problems. We offer a comprehensive list of suggestions for keeping WordPress admin secure.
You may, for example, make the wp-admin directory password-protected. This adds another degree of complexity.
This provides additional layer of security to your website’s most essential entrance point.
You may also restrict access to the admin section to your team’s IP addresses. Another option to keep hackers out if they figure out your login and password is to utilise this method.
5. Turn off the Editors for Themes and Plugins
WordPress has a built-in theme and plugin editor, in case you didn’t know. You may change your theme and plugin files directly from the WordPress dashboard with this plain text editor.
While this is beneficial, it may cause security concerns. If a hacker gains access to your WordPress admin area, for example, they can utilise the built-in editor to access all of your WordPress data.
, they’ll be able to use your WordPress site to spread malware or perform DDoS assaults.
We propose totally deleting the built-in file editors to boost WordPress security.
6. Turn off PHP execution in specific WordPress folders
PHP scripts can be launched in any folder on your website by default. You may improve the security of your website by turning off PHP execution in directories that don’t require it.
WordPress, for example, never needs to run code from your uploads folder. If you stop PHP execution for that folder, even if a hacker successfully uploads one, they won’t be able to run it.
7. Ensure that your website is up to date.
Every new WordPress version is more secure than the previous one. Whenever a security breach occurs,
When a security vulnerability is discovered, the WordPress core team works quickly to deliver an update that addresses the problem.
This implies that if you don’t keep WordPress updated, you’re using software that has known security flaws. Hackers can look for websites that are running an earlier version and exploit the flaw.
As a result, you should always utilise the most recent WordPress version.
Keep WordPress up to date, but don’t stop there. You must also ensure that your WordPress plugins and themes are up to date.
We hope that this guide taught you how to locate and repair a backdoor in a hacked WordPress site. You might also want to check out how to switch WordPress from HTTP to HTTPS.